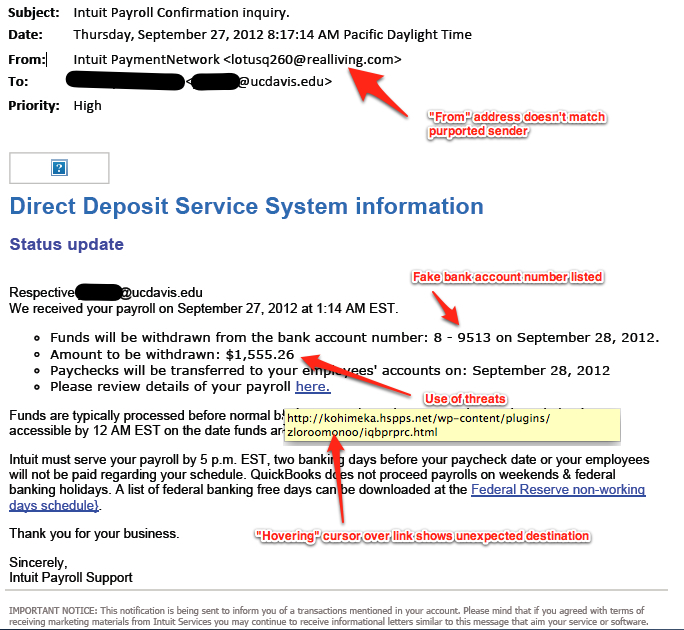
The Royal Canadian Numismatic Association sent email to its members notifying them that on April 24 someone attempted a phishing scam trying to impersonate the RCNA Executive Secretary trolling for information. The RCNA did not send out an email note asking for information and recommended deleting them email.
The Royal Canadian Numismatic Association sent email to its members notifying them that on April 24 someone attempted a phishing scam trying to impersonate the RCNA Executive Secretary trolling for information. The RCNA did not send out an email note asking for information and recommended deleting them email.
Phishing is the term used to describe the attempt to convince someone to reveal personal information by sending them an email that looks like it came from a legitimate source. In this case, the attacker made their email look like it came from the RCNA hoping that members would give up their personal information.
When I am not blogging, meeting with other numismatists, or being with my family, I work in information security for the United States federal government. In my professional life, I have seen a lot of attempted and successful attacks against both government and commercial systems. However, the one attack that is the most difficult to defend are those where humans are convinced to act against their own best interest, such as a phishing attack.
Social engineering attacks are my favorite attacks. One reason is that it helps demonstrate to the organizations that I try to help that security is more than controls, encrypted communications, or anything else you might have read in the news. Security is a process that requires diligence, the same as it does in the real world.
The following are four rules that you can follow to help keep safe online:
Rule #1: Unless you are 100-percent certain that the email is legitimate, do not click on the link!
You will be never 100-percent certain that any email you receive is legitimate so make sure that you are as close as 100-percent certain as possible. One thing you can do is to move your pointer over the link, stop, and wait for the tooltip to show you the address.
Tooltips are those balloon-like popups that will tell you something about the link or element before you press the mouse button. One way to tell that a link is bad is that if the address is not what you think. For example, if the link is supposed to send you to the RCNA website, the tooltip better say that it will send you to rcna.ca. If it does not, then do not click on the link.
When you check the link, the address of the server is the first part of the address. If what should be the server name is not in that area at the beginning of the address, do not click on the link.
One trick the phishers use is to show you what looks like a complicated address in the message, but the link behind it will send you to another website. This is where tooltips can help. If you hover over the address and they do not match, it is an attempt to trick you and you should not click on the link.
If you are using a web-based email client, you can check the address on the status line at the bottom of your browser window. Check to see if the address makes sense is also a good tool. For example, if the link is supposed to be from the RCNA and “rcna.ca” is not the address of the server in the link, then it is a phishing attempt and you should not click on the link.
If you are unsure about the link, then go to your browser and type in the address yourself. Rather than clicking on a suspicious link, you can visit the RCNA website by typing “http://rcna.ca” directly into your browser’s address bar.
Rule #2: No legitimate company or organization will send you a form to fill out and email back
One of the tactics that the phishers use to try to trick you into giving them your personal information is to create a form that looks like it is legitimate. Just as it is easy for someone with moderate skills to fake a web page, they can create a counterfeit form. Not only will the form be counterfeit, but they could also embed programs in that form to steal your information.
Embedded code in documents is called macros. Macros are used to command programs to do something for the user. When used in productive environment, macros can be a wonderful tool to create dynamic documents. But the same instructions that can make macros a productive tool can also be used to do bad things.
Unless you are certain about where the document came from, then do not open a document. If you open the document and the program asks if you should enable or run macros, do not enable macros.
This is not just a problem with word processing document. PDF documents can also deliver very nasty malware (malicious software). Not only can an attacker add macros to a PDF document, but someone can embed the technology called Flash in those PDF. Flash is the technology that helps you see videos and add enhancements to the visual interface of some websites. But Flash can be used to attack your computer system. Opening a PDF file sent by someone you do not know can be as dangerous as a word processing document.
Rule #3: Do not open suspicious attachments
Another trick the attackers try to use is adding an attachment named in a way to try to trick you into opening the file. File names consist of the name of a file followed by a period followed by a file extension. The file extension is used to tell the computer the type of program to open to allow you to work with the file. There are three file extension that very dangerous and should never be opened unless you are absolutely sure who sent them to you: .zip, .exe, and .dmg for Mac users.
The .zip file extension tells the computer that the file is something called a Zip archive. A Zip archive is a file that is formatted to allow it to store many files that are compressed. Zip files are used for many legitimate purposes including being the default format of Microsoft Word’s .docx file. Unfortunately, it can contain files that can be used to attack your system.
One of the types of file that can be included in a Zip archive is an .exe or executable file. Simply, these are programs in the same way that Microsoft Word is a program. Once an executable file is opened, it will do whatever it is programmed to do. Among the things that the program can do is key logging. A key logger reads what you type on your keyboard, what you click on the screen, and in some cases what is displayed on your screen. The key logger will be able to capture the user name and password you entered when you visit any website including your bank’s website. The problem is that when a key logging program is run, you do not know it is watching what you type. Nor do you know that it connects to a server somewhere on the Internet to send the information to the attacker.
While Macs are more difficult to attack, they are not immune. Mac users should never open a file with a .dmg file extension unless you know who sent the file. The Macintosh .dmg file is a disk image file. A disk image file is formatted to look and acts like a disk so that when you double click the file, it will mount on your computer as if you plugged in an external disk drive. Because .dmg files are commonly used to install legitimate software, sometimes the installation can be automatically started. If you allow the installation to continue, it you can install software as dangerous as what I described for the Windows .exe file.
Rule #4: When in doubt, throw it out!
 While all this seems simple to me, I have been in this industry for over 30 years and am used to the complication. The problem with email is that it was developed as a way for researched to communicate by plain text across the Arpanet, the forerunner of the Internet. Essentially, email is a text-based service that has been extended in so many ways that it has created a complicated series of standards that requires a degree in computer science to analyze.
While all this seems simple to me, I have been in this industry for over 30 years and am used to the complication. The problem with email is that it was developed as a way for researched to communicate by plain text across the Arpanet, the forerunner of the Internet. Essentially, email is a text-based service that has been extended in so many ways that it has created a complicated series of standards that requires a degree in computer science to analyze.
Even if you cannot fully analyze whether the message is spam or legitimate, if you have any doubt, then just press the delete button. If the message came from a source you know, contact them off line and ask if the mail is legitimate. If you think the email is from your bank, call the bank and ask. If you think the email is from your credit card company but not sure, call the credit card provider and ask. If you think the email sent from the RCNA is suspicious, call them and make and ask.
A little intuition can be of great help in these circumstances.
Stay safe online and have a good weekend!