Oct 19, 2021 | coins, news, security
 One of the reasons for the delay with the Weekly World Numismatic News is that I have been looking into a report of worldwide e-commerce issues under the radar.
One of the reasons for the delay with the Weekly World Numismatic News is that I have been looking into a report of worldwide e-commerce issues under the radar.
After ordering a box of flips and other storage products from a small company, a representative called to say that the transaction did not go through. According to the representative, overseas attackers are trying to hack shopping cart sites to steal merchandise and credit card information. Rather than attacking the entire site, the hackers are targeting individual shops. They are looking for sites that are not configured correctly.
During the telephone call, the representative said they turned off credit card verification and the system “throws the credit card away.” I know this vendor, but I am still not comfortable.
E-commerce is supposed to make purchasing goods and services more accessible. But when hackers are driving vendors to verify credit cards by telephone, it is not making e-commerce easy. Thankfully, I received an announcement for local shows. Maybe it’s time to spend money there.
By the way, a source told me that the Baltimore Convention Centre would be open when the Whitman Expo is scheduled in November.
And now the news…

October 8, 2021
Subscribe now! EUREKA — Walker Hilbert sat on the ground one recent Saturday, next to a small mound of dirt. He waved a wand above the soil, and the device chirped encouragingly.

→ Read more at
stltoday.com

October 14, 2021
King County sheriff warns of counterfeit bills FALL CITY, Wash. — A Fall City grocery store fell victim to a man using a counterfeit $100 bill Tuesday, according to the King County Sheriff’s Office.

→ Read more at
kiro7.com
Jul 22, 2021 | security, silver, US Mint
This is the second article of three regarding the recent problems at the U.S. Mint.

It is as if the U.S. Mint did not learn a lot since the fiasco of the 2014 Kennedy Half Dollar 50th Anniversary Gold Coin release. (Image courtesy of ABC 7 News, Denver)
Last month, a discussion was held with a representative of the U.S. Mint’s communications department and a manufacturing supervisor to understand better the 2021 Morgan Dollar ordering failures. When asked about lessons learned from previous sales, they admitted to working at the U.S. Mint for four years or less and could not talk about previous issues.
After asking about lessons learned from the past with responses ringing like “not on my watch,” it brought to mind the first Numismatic Forum in 2016, where the only blogger in attendance asked whether the discussions would survive changes of leadership and administrations. Rhett Jeppson was nominated to be Director of the U.S. Mint but was never confirmed. Although there were three more Numismatic Forums, it is apparent that none of the discussions survived leadership changes.
Part of the problem is with the government’s Senior Executive Service (SES) program. Members of the SES are government employees hired to senior management positions within the federal government. They undergo special training in government leadership and understand how to lead their sections through policy changes. SES employees are supposed to be non-partisan government workers. There are also limited reasons for the SES to stay with the agency to build collective knowledge.
There are three ways an SES employee can be appointed. A career appointment is a merit position staffed by a qualified executive. A noncareer appointment is a temporary appointment and is subject to several restrictions, including the number of temporary appointees the government can hire. Finally, a limited appointment is hired for an 18 month to a three-year term. Rhett Jeppson’s role that made him the acting Director was the result of a limited appointment.
SES members are also encouraged to change agencies every four years. Although there are exceptions, the SES program is designed not to allow executives to become too powerful within the agencies. Forcing them to move reduces the risk of potential abuse of power.
As SES members come and go, the U.S. Mint loses the institutional knowledge they earned over the years. Experience working with members of the SES program shows that the new appointees rarely refer to documentation left by their predecessors. Their egos also have them ignoring employees and contractors with the institutional knowledge.
The U.S. Mint has resources in the numismatic community that can help teach them about the past. Having an engaged numismatic community available to help the U.S. Mint makes the bureau unique among government agencies. If their egos prevent them from reaching out to the numismatic community, the SES members can perform a web search on any topic to read what the numismatic press wrote about any issue.
During the discussion, the U.S. Mint emphasized how they wanted to work with the numismatic community and do their best to make the products accessible. While they will talk with members of the numismatic media, the U.S. Mint will not reach out for the community’s help.
The numismatic community wants the U.S. Mint to be able to support our collecting habits. They have a unique opportunity to engage a community willing to help. If the U.S. Mint wants to demonstrate that they are, they should set up a program of numismatic advisors to help them understand what went wrong in the past and how to make it better for the future.
If you like what you read, share, and show your support 
Jul 21, 2019 | commentary, news, security
 While there was plenty of news this week, I want to take this opportunity to use myself as an example. Some may have noticed that the blog was taken down for a little more than a day earlier this week. The downtime was necessary to clean up after my account was attacked.
While there was plenty of news this week, I want to take this opportunity to use myself as an example. Some may have noticed that the blog was taken down for a little more than a day earlier this week. The downtime was necessary to clean up after my account was attacked.
The attack occurred after I had given the person who is maintaining my company’s website the administrative passwords. Although that person did not attack my account, the use of compromised services on the Internet allowed the attack to happen.
Being attacked by malware on the Internet is nothing new. I am sure that most of you experienced an attack either of a website, your email, or social media account. The clean up is not fun. The embarrassment after spending a career as an information security profession is enormous.
I do pay attention to my version of the world to make sure that what I am involved with does not cause problems. Even so, something got passed my watch and infected my entire account, including this blog and the news site.
I have written about security issues in the past. As my experience has shown, letting down your guard can lead to an unintentional disaster.
I know that Internet security is both problematic and annoying. Having to watch over your virtual shoulders can make the time you spend online unpleasant. But it has to be done. You have to stay aware because the threats adapt as you do.
Fans of Hill Street Blues will remember that after the morning briefing, Sergeant Phil Esterhaus would say, “Let’s be careful out there.” Sound advice for the Internet age.
And now the news…

July 14, 2019
London (CNN Business)Alan Turing, a crack code-breaker and visionary mathematician who was convicted under Victorian-era homophobic laws, will be the face of Britain's new £50 note. Bank of England Governor Mark Carney announced Monday that Turing, who killed himself in 1954 after he was subjected to chemical castration, will appear on the new polymer note by the end of 2021.  → Read more at cnn.com
→ Read more at cnn.com

July 17, 2019
Nick Vorsin wasn’t sure what he’d find when he stopped in at the Calgary Coin Gallery, but he ended up buying a couple of nice surprises: two 1967 Canadian Centennial coins. One was a 50 cent piece, featuring an image of a howling wolf, along with a silver dollar featuring a Canada goose.  → Read more at globalnews.ca
→ Read more at globalnews.ca

July 17, 2019
(UPDATED) A study finds that Filipinos frequently use P20 bills, leading to the banknote's wear and tear. A coin version will extend its life span. MANILA, Philippines (UPDATED) – The orange P20 bill will soon get a coin counterpart, an official of the Bangko Sentral ng Pilipinas (BSP) said on Wednesday, July 17.  → Read more at rappler.com
→ Read more at rappler.com

July 18, 2019
Before you say, "Keep the change," make sure you don’t have one of these. You never know, one of your pennies could be worth the price of a nice dinner out — or maybe a whole lot more.  → Read more at cnbc.com
→ Read more at cnbc.com

July 21, 2019
Richard Hayes left a $45 million coin on the streets of Manhattan all day Tuesday, but he wasn’t particularly worried about a thief carting it off.  → Read more at marketwatch.com
→ Read more at marketwatch.com

July 21, 2019
Rusty Goe has spent much of his professional life on a deep dive into the history of the U.S. Mint in Carson City. He’s written multiple books on the subject and spent thousands of hours in research, getting to know the people who worked there 150 years ago.  → Read more at carsonnow.org
→ Read more at carsonnow.org

July 21, 2019
There was an increase in hoarding coins during the "tumultuous" reign of the queen, an expert says.  → Read more at bbc.com
→ Read more at bbc.com
Apr 7, 2018 | advice, education, security
 The American Numismatic Association and Numismatic Guarantee Corporation recently issued press releases notifying the public that there have been attempted phishing scams by trying to impersonate a hotel service or someone who works for NGC. Since this is back in the news, I am taking an article I had previously written on the topic and updating it to be more current.
The American Numismatic Association and Numismatic Guarantee Corporation recently issued press releases notifying the public that there have been attempted phishing scams by trying to impersonate a hotel service or someone who works for NGC. Since this is back in the news, I am taking an article I had previously written on the topic and updating it to be more current.
Phishing is the term used to describe the attempt to convince someone to reveal personal information by sending them an email that looks like it came from a legitimate source. Unfortunately, it is so easy to spoof (trick) the Internet’s email system that all it takes is someone with attention to detail to get past spam and other security filters.
Last year, I retired as an information security professional where, for the last 25 years, was contracting to the United States government. I saw many attempted and successful attacks against both government and commercial systems. However, the one attack that is the most difficult to defend is those where humans are convinced to act against their own best interest. The technical industry calls them phishing attack but they are forms of social engineering.
A social engineering attack tries to use something about you or something you care about to convince you to do something that could potentially harm you. For example, an attacker looking to scam someone who collects rare coins may know about NGC’s business. Knowing that the people who might be using NGC’s services are collectors with a lot of disposable income, they could use the weaknesses of the email system in order to fool the recipient into a situation where they can be taken advantage of.
To help you stay safe, the following are rules you can follow to keep safe online:
Rule #1: Unless you are 100-percent certain that the email is legitimate, do not click on the link!
You will be never 100-percent certain that any email you receive is legitimate. Thus, make sure that you are as close as 100-percent certain as possible. One thing you can do is to move your pointer over the link, stop, and wait for the tooltip to show you the address.
Tooltips are those balloon-like popups that will tell you something about the link or element before you press the mouse button. One way to tell that a link is bad is that if the address is not what you think. For example, if the link is supposed to send you to the ANA website, the tooltip better say that it will send you to money.org. If it does not, then do not click on the link.
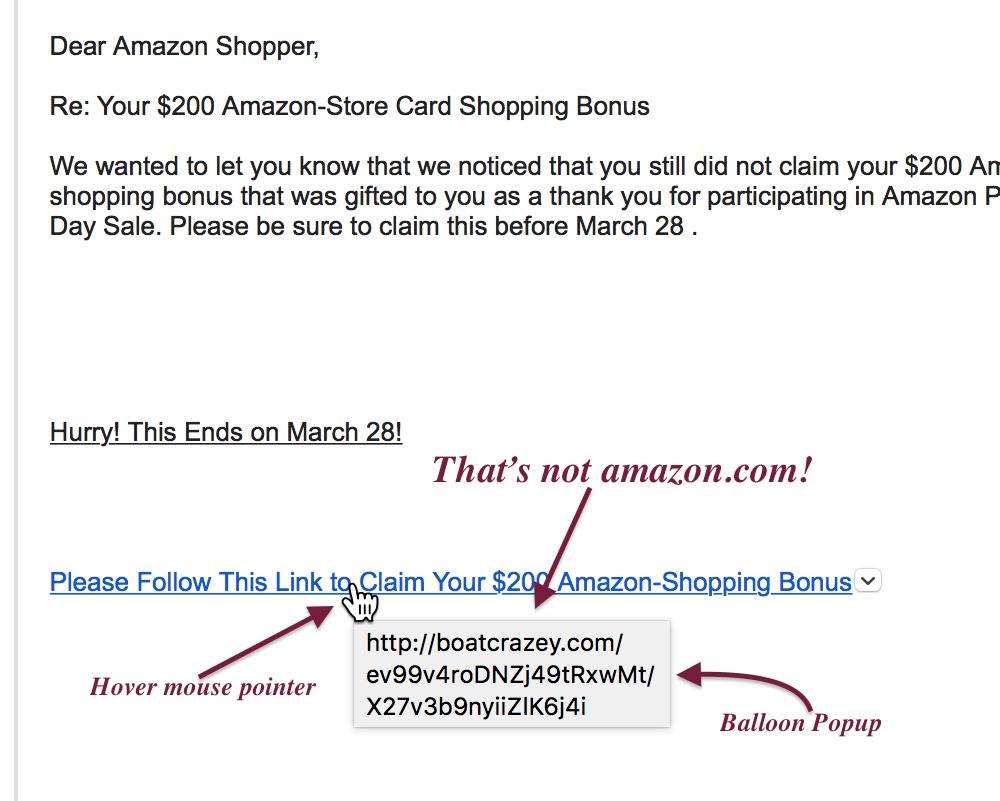
Place your mouse pointer over the link and let the tool tip appear. What does it say?
When you check the link, the address of the server is the first part of the address. If what should be the server name is not in that area at the beginning of the address, do not click on the link.
One trick the phishers use is to show you what looks like a complicated address in the message, but the link behind it will send you to another website. This is where tooltips can help. If you hover over the address and they do not match, it is an attempt to trick you and you should not click on the link.
If you are using a web-based email client, such as Gmail, you can check the address on the status line at the bottom of your browser window. Check to see if the address makes sense. For example, if the email claims to be from Amazon, the link should say “amazon.com” and nothing else. Sometimes phishers will try to write a link using something after the address like “amazon.com.anothersite.co” to fool you. Do not be fooled. A link like this is trying to send you to “anothersite.co” and not Amazon.
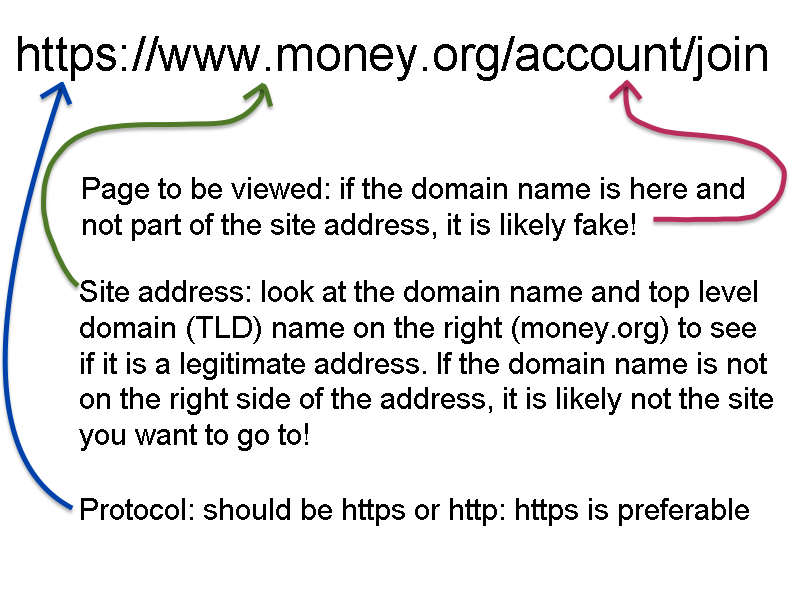
Understanding the part of a typical URL and what to look for
If you are unsure about the link, then go to your browser and type in the address yourself.
As with everything in life, there is an exception to the rule. Organizations, like the ANA, will use mailing list services to send out notices to members and anyone else who have signed up for these emails. Unfortunately, the URL you will click on will be one associated with the mailing list service. The service uses this to provide engagement statistics to whoever is sending out the email. For example, for the service that the ANA uses all of the links are to r.listpilot.com.
Mailing list services are great resources for many organizations and their tracking service is necessary to understand the effectiveness of the communication. If you are not sure, continue to visit the organization’s site without clicking on the link.

An example of an email message showing what to look for to understand how to identify it as a phishing attempt.

Examine the envelope information, also referred to as the headers of the message, for signals that this could be a phishing attempt.

Even though a lot of email contains grammatical errors, businesses have proof readers that will prevent the most egregious errors. Look for bad spelling and even using numbers instead of characters, such as using a zero instead of a capital “O.”
Rule #2: No legitimate company or organization will ask for information to be sent via email
One of the tactics that the phishers use to try to trick you into giving them your personal information is to create a form that looks like it is legitimate. Just as it is easy for someone with moderate skills to fake a web page they can also create a counterfeit form. Not only will the form be counterfeit, but they could also embed programs in that form to steal your information.
Embedded code in documents is called macros. Macros are used to command programs to do something for the user. When used in productive environments, macros can be a wonderful tool to create dynamic documents and provide input validation. But the same instructions that can make macros a productive tool can also be used to do bad things.
Unless you are certain about where the document came from, do not open a document. If you open the document and the program asks if you should enable or run macros, do not enable macros.
This is not just a problem with word processing document. PDF documents can also deliver very nasty malware (malicious software). Not only can an attacker add macros to a PDF document, but someone can embed Flash in those PDF. Flash is the technology that helps you watch online videos and add enhancements to the visual interface of some websites. But Flash can be used to attack your computer system. Opening a PDF file sent by someone you do not know can be as dangerous as a word processing document.
Rule #3: Do not open suspicious attachments
Another trick the attackers try to use is adding an attachment named in a way to entice you to open the file. File names consist of the name of a file followed by a period followed by a file extension. The file extension is used to tell the computer the type of program to execute to allow you to work with the file. There are three file extension that very dangerous and should never be opened unless you are absolutely sure who sent them: .zip, .exe, and .dmg for Mac users.
The .zip file extension tells the computer that the file is something called a Zip archive. A Zip archive is a file that is formatted to allow it to store many files that are compressed. Zip files are used for many legitimate purposes including being the default format of Microsoft Word’s .docx file. Unfortunately, it can contain programs and files that can be used to attack your system.
One of the types of file that can be included in a Zip archive is a .exe or executable file. Simply, these are programs in the same way that Microsoft Word is a program. Once an executable file is opened, it will do whatever it is programmed to do. Among the things that the program can do is keylogging. A keylogger reads what you type on your keyboard, what you click on the screen, and in some cases, what is displayed on your screen. The keylogger will be able to capture the username and password you entered when you visit any website including your bank’s website. The problem is that when a key logging program is run, you do not know it is watching what you type. Nor do you know that it connects to a server somewhere on the Internet to send the information to the attacker. Keyloggers and other malware can infect your system in a way that allows it to continue to exist, even if you reboot the computer.
You may ask about anti-virus software helping stop malware. Anti-virus software is programmed to understand what is known about attack vectors. It cannot protect you if it does not know how the virus works. Remember that the government warned that last year’s flu vaccine was not effective for the version of the virus infecting people? Anti-virus software is similar that if it doesn’t know about the strain it cannot protect you. Hackers are always looking for ways to fool anti-virus software.
For Windows user, you should consider running Windows Defender. Windows Defender is built into Windows but cannot be run if you have another anti-virus software. I use Windows Defender and have been happy with the results. If you want more information about Windows Defender visit this page on Microsoft’s support site.
While Macs are more difficult to attack they are not immune. Mac users should never open a file with a .dmg file extension unless you know who sent the file. The Macintosh .dmg file is a disk image stored as a regular file. A disk image file is formatted to look and acts like a disk so that when you double-click the icon, it will mount on your computer as if you plugged in an external disk drive. Because .dmg files are commonly used to install legitimate software, sometimes the installation can be automatically started. If you allow the installation to continue, you can install software as dangerous as what I described for the Windows .exe file.
OS X is a different type of operating system where if you are careful you can get away without running an anti-virus program. However, if you want to be paranoid (along with me) you might want to run the free anti-malware software from Malware Bytes.
Regardless of the operating system and software you use, ALWAYS KEEP IT UP TO DATE! Patching your computer may be an annoyance but the dangers, if you do not apply security patches, will hurt more and last longer!
Rule #4: When in doubt, throw it out!
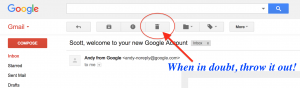 While all this seems simple to me after having worked in this industry for nearly 40 years, I have seen how these concepts are confusing to the non-technical user. The problem with email is that it was developed as a way for researchers to communicate by plain text across Arpanet, the forerunner of the Internet. Email, as a text-based service, \ has been extended in so many ways that it has created a complicated series of standards that require a degree in computer science to analyze. While these complications make it easier to communicate via email it also makes it difficult to secure.
While all this seems simple to me after having worked in this industry for nearly 40 years, I have seen how these concepts are confusing to the non-technical user. The problem with email is that it was developed as a way for researchers to communicate by plain text across Arpanet, the forerunner of the Internet. Email, as a text-based service, \ has been extended in so many ways that it has created a complicated series of standards that require a degree in computer science to analyze. While these complications make it easier to communicate via email it also makes it difficult to secure.
Even if you cannot fully analyze whether the message is spam or legitimate, if you have any doubt, then just press the delete button. If the message came from a source you know, contact them off-line and ask if the mail is legitimate. If you think the email is from your bank, call the bank and ask. If you think the email is from your credit card company but not sure, call the credit card provider and ask. If you think the email sent from the ANA or NGC is suspicious, call them and ask.
A little intuition and some due diligence can be of great help in these circumstances.
Stay safe online!
Mar 31, 2018 | administrative, advice, ANA, security, shows
Normally, I do not directly publish news items but this is important for the entire community.
Did you receive an email or call trying to sell you a Philadelphia World’s Fair of Money hotel room?
The ANA did not authorize this.
It has come to our attention that a third-party booking company inaccurately representing itself as our hotel vendor is contacting ANA members, dealers and exhibitors, offering to book you a hotel room at the ANA World’s Fair of Money; some even provide a promotion code or will misrepresent that they are calling from the hotel.
ANA is not utilizing any housing service vendors for the Philadelphia World’s Fair of Money. Nor has the ANA shared your email with anyone.
Room reservations for the Philadelphia World’s Fair of Money should be made directly with the Philadelphia Marriot Downtown (the show’s host hotel) either by phone – 1-888-236-2427 (mention ANA World’s Fair of Money to secure the group rate) – or via our website at www.money.org/worldsfairofmoney/lodging. Should you want to stay elsewhere, we strongly recommend calling the hotel directly or using a reputable online service such as Hotels.com or Expedia.com.
If you provide your credit card information to any of these unauthorized vendors, your card may be charged but you may not have a reservation when you arrive in Philadelphia. Unfortunately, this is a well-known scam perpetuated on unsuspecting conventioneers across the country.
If you have any questions about the World’s Fair of Money hotel block, or general questions about the show, please contact Jennifer Ackerman at ackerman@money.org, Christie Cooper at ccooper@money.org, or call the ANA Convention team at 1-888-448-3262. Complete information about the show is also available online at www.worldsfairofmoney.com.

Feb 22, 2018 | commentary, counterfeit, currency, education, scams, security
It is difficult to turn on the television, read the news, or visit social media without the tragedies of the day smacking us in the face. Although crime statistics are the lowest it has been in generations, there are some crimes that have seen a rise. Those are the crimes that are given the headlines and the most airtime on the news.
Unfortunately, the news extends beyond the mainstream but extends to Main Street.
Numismatics has not been a stranger to the criminal element. If it is not embezzlers using coins to defraud people and governments, there are the counterfeits primarily coming from China. Now there are two new scams that the industry has to watch.
Counterfeiting currency is definitely not a new issue. Counterfeiting the currency that is supposed to be the most secure is something that is now hitting the mainstream, especially in countries that have adopted the use of polymer notes, is important news.
Police in Saskatoon, Saskatchewan has reported the confiscation of 72 bogus Canadian banknotes. Counterfeiters are using a combination of printed plastic sheets and physical cut-and-paste of lower denomination notes to mimic higher denomination notes.

Image released by the Saskatoon Police showing the counterfeit currency (Image courtesy of the Saskatoon Police via the Saskatoon StarPhoenix)
Within the same news feed, the Bank of England issued warnings and additional guidance after counterfeit notes were used for purchases at pubs in Lincolnshire. Many stories from the U.K. suggest that the people do not seem to like the new polymer notes, but this does not seem to help.

Bank of England wants people to watch for the color shifting ink in the quill (Bank of England image)
The Reserve Bank of Australia (RBA), Australia’s central bank and the primary developer of the polymer substrate used around the world, has found that their currency is under attack by industrious forgers. One particular forger found a plastic substrate similar to the polymer developed by the RBA. The forger bought one high-quality commercial printer from the used market and rented two others to print Australian $50 notes.
According to the reports, the $50 note was picked because it provides is common enough to be used in daily transactions (AU$50 is equivalent to US$39.06 as this is being written) and high enough of a denomination to be cost-effective for the forger. Remember, forgery may be a crime but it is a business.

A counterfeit Australian $50 note has the wrong security stripes and the star field on the right is supposed to be clear (Image courtesy of The Sydney Morning Herald)
Although these issues have not directly affected the collectible currency market, it has had an effect on the dealers when their customers pay in cash. Even with the rise of electronic transactions, many European dealers continue to do over-the-counter sales using cash. In some countries, like Germany, cash is still king even when purchasing rare coins.
While discussing these issues with a dealer based in Germany, it was reported that he will not accept large sums of cash from customers he has not done business with in the past. This dealer does not accept credit card payments over 200€ or for any bullion-based transactions. His regular customers can directly wire the funds to a special account the dealer set up. Others must use certified bank checks.
This is not to suggest wire transfers are safe. In a blog post on Kovels.com, they have been contacted by antique dealers that reported money stolen by wire transfers. According to the blog post:
The fraudsters hack your emails and insert their own email, cloned to look like an email from a trusted person, into your email stream. They then request a wire transfer — providing all needed wire instructions — for something that looks legitimate. Once a bank wire is sent, it is extremely difficult, if not impossible, to get the money back. If you need to send a wire, be sure to use “old” technology and confirm on the telephone with someone that you know!
Even though I am no longer in the information security business, it is still my obligation to remind you that EMAIL IS NOT A SECURE FORM OF COMMUNICATION! Email is the electronic equivalent of a postcard. Any message you send, unless it is encrypted, can be read, scanned, snooped, and even altered by anyone, anywhere, at any time.
“Oh, it cannot happen to me!”
I used to hear that line when I taught a senior-level college class on information security. Using a laptop connected to an overhead projector, I was able to show the class how easy it was not only to create spam but to make it look like an email was sent by someone else. I was also able to demonstrate how to read the email traffic on the local network with a few keystrokes. Are you using wireless connections? You just made stealing your information easier for the hacker.
Counterfeiting and wire fraud are not just problems for dealers. When dealers are defrauded by these criminals, they have to recover the money in some way. Insurance does not cover all losses or the extra security that will be required to protect their transactions. Prices will have to go up to cover the losses and the future costs of doing business.
The cost of doing business in this environment is not a trivial subject. While dealers of all types of collectibles want you business, fraudsters are making it difficult for dealers trust the off-the-street buyer. This makes counterfeiting and fraud a problem for everyone.
Apr 26, 2014 | advice, education, security, technology, web
 The Royal Canadian Numismatic Association sent email to its members notifying them that on April 24 someone attempted a phishing scam trying to impersonate the RCNA Executive Secretary trolling for information. The RCNA did not send out an email note asking for information and recommended deleting them email.
The Royal Canadian Numismatic Association sent email to its members notifying them that on April 24 someone attempted a phishing scam trying to impersonate the RCNA Executive Secretary trolling for information. The RCNA did not send out an email note asking for information and recommended deleting them email.
Phishing is the term used to describe the attempt to convince someone to reveal personal information by sending them an email that looks like it came from a legitimate source. In this case, the attacker made their email look like it came from the RCNA hoping that members would give up their personal information.
When I am not blogging, meeting with other numismatists, or being with my family, I work in information security for the United States federal government. In my professional life, I have seen a lot of attempted and successful attacks against both government and commercial systems. However, the one attack that is the most difficult to defend are those where humans are convinced to act against their own best interest, such as a phishing attack.
Social engineering attacks are my favorite attacks. One reason is that it helps demonstrate to the organizations that I try to help that security is more than controls, encrypted communications, or anything else you might have read in the news. Security is a process that requires diligence, the same as it does in the real world.
The following are four rules that you can follow to help keep safe online:
Rule #1: Unless you are 100-percent certain that the email is legitimate, do not click on the link!
You will be never 100-percent certain that any email you receive is legitimate so make sure that you are as close as 100-percent certain as possible. One thing you can do is to move your pointer over the link, stop, and wait for the tooltip to show you the address.
Tooltips are those balloon-like popups that will tell you something about the link or element before you press the mouse button. One way to tell that a link is bad is that if the address is not what you think. For example, if the link is supposed to send you to the RCNA website, the tooltip better say that it will send you to rcna.ca. If it does not, then do not click on the link.
When you check the link, the address of the server is the first part of the address. If what should be the server name is not in that area at the beginning of the address, do not click on the link.
One trick the phishers use is to show you what looks like a complicated address in the message, but the link behind it will send you to another website. This is where tooltips can help. If you hover over the address and they do not match, it is an attempt to trick you and you should not click on the link.
If you are using a web-based email client, you can check the address on the status line at the bottom of your browser window. Check to see if the address makes sense is also a good tool. For example, if the link is supposed to be from the RCNA and “rcna.ca” is not the address of the server in the link, then it is a phishing attempt and you should not click on the link.
If you are unsure about the link, then go to your browser and type in the address yourself. Rather than clicking on a suspicious link, you can visit the RCNA website by typing “http://rcna.ca” directly into your browser’s address bar.
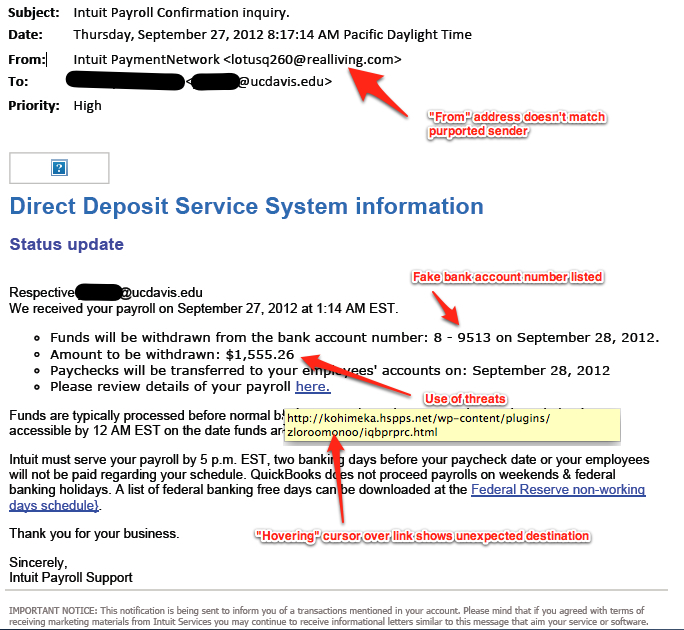
Anatomy of a Phishing email
(courtesy of the University of California-Davis)
Rule #2: No legitimate company or organization will send you a form to fill out and email back
One of the tactics that the phishers use to try to trick you into giving them your personal information is to create a form that looks like it is legitimate. Just as it is easy for someone with moderate skills to fake a web page, they can create a counterfeit form. Not only will the form be counterfeit, but they could also embed programs in that form to steal your information.
Embedded code in documents is called macros. Macros are used to command programs to do something for the user. When used in productive environment, macros can be a wonderful tool to create dynamic documents. But the same instructions that can make macros a productive tool can also be used to do bad things.
Unless you are certain about where the document came from, then do not open a document. If you open the document and the program asks if you should enable or run macros, do not enable macros.
This is not just a problem with word processing document. PDF documents can also deliver very nasty malware (malicious software). Not only can an attacker add macros to a PDF document, but someone can embed the technology called Flash in those PDF. Flash is the technology that helps you see videos and add enhancements to the visual interface of some websites. But Flash can be used to attack your computer system. Opening a PDF file sent by someone you do not know can be as dangerous as a word processing document.
Rule #3: Do not open suspicious attachments
Another trick the attackers try to use is adding an attachment named in a way to try to trick you into opening the file. File names consist of the name of a file followed by a period followed by a file extension. The file extension is used to tell the computer the type of program to open to allow you to work with the file. There are three file extension that very dangerous and should never be opened unless you are absolutely sure who sent them to you: .zip, .exe, and .dmg for Mac users.
The .zip file extension tells the computer that the file is something called a Zip archive. A Zip archive is a file that is formatted to allow it to store many files that are compressed. Zip files are used for many legitimate purposes including being the default format of Microsoft Word’s .docx file. Unfortunately, it can contain files that can be used to attack your system.
One of the types of file that can be included in a Zip archive is an .exe or executable file. Simply, these are programs in the same way that Microsoft Word is a program. Once an executable file is opened, it will do whatever it is programmed to do. Among the things that the program can do is key logging. A key logger reads what you type on your keyboard, what you click on the screen, and in some cases what is displayed on your screen. The key logger will be able to capture the user name and password you entered when you visit any website including your bank’s website. The problem is that when a key logging program is run, you do not know it is watching what you type. Nor do you know that it connects to a server somewhere on the Internet to send the information to the attacker.
While Macs are more difficult to attack, they are not immune. Mac users should never open a file with a .dmg file extension unless you know who sent the file. The Macintosh .dmg file is a disk image file. A disk image file is formatted to look and acts like a disk so that when you double click the file, it will mount on your computer as if you plugged in an external disk drive. Because .dmg files are commonly used to install legitimate software, sometimes the installation can be automatically started. If you allow the installation to continue, it you can install software as dangerous as what I described for the Windows .exe file.
Rule #4: When in doubt, throw it out!
 While all this seems simple to me, I have been in this industry for over 30 years and am used to the complication. The problem with email is that it was developed as a way for researched to communicate by plain text across the Arpanet, the forerunner of the Internet. Essentially, email is a text-based service that has been extended in so many ways that it has created a complicated series of standards that requires a degree in computer science to analyze.
While all this seems simple to me, I have been in this industry for over 30 years and am used to the complication. The problem with email is that it was developed as a way for researched to communicate by plain text across the Arpanet, the forerunner of the Internet. Essentially, email is a text-based service that has been extended in so many ways that it has created a complicated series of standards that requires a degree in computer science to analyze.
Even if you cannot fully analyze whether the message is spam or legitimate, if you have any doubt, then just press the delete button. If the message came from a source you know, contact them off line and ask if the mail is legitimate. If you think the email is from your bank, call the bank and ask. If you think the email is from your credit card company but not sure, call the credit card provider and ask. If you think the email sent from the RCNA is suspicious, call them and make and ask.
A little intuition can be of great help in these circumstances.
Stay safe online and have a good weekend!
Apr 11, 2014 | advice, coins, security, technology
 Computer and online security has been a topic for the news lately. This was because of a mistake made in software that was being used to try to keep your password from being seen by criminal hackers was making it visible to those criminals. In the wake of the news, the Doug Davis of the Numismatic Crime Information Center sent out a message to his list of contacts that had one central message for every dealer and collector:
Computer and online security has been a topic for the news lately. This was because of a mistake made in software that was being used to try to keep your password from being seen by criminal hackers was making it visible to those criminals. In the wake of the news, the Doug Davis of the Numismatic Crime Information Center sent out a message to his list of contacts that had one central message for every dealer and collector:
Shooting simple photos from your smart phone or personal camera can lead criminals right to your location… with pinpoint accuracy using GPS satellites.
You might have heard the term “metadata” in the news in the context of its collection by the National Security Agency. For those who do not know what metadata is, think of it as a description of the data. Think about an exhibit in a museum. The exhibit contains several artifacts arranged in a certain way to try to tell a story. But the story is incomplete because a little more information is needed to put it into context. But the information cannot be shown as an artifact in the exhibit, so the person setting up the exhibit adds a description added to the exhibit to make it more understandable. That description would be the metadata to the exhibit.
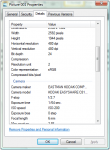
Example of what you can find out about your image in the file’s Properties under Windows
Modern cameras, cameras built into smartphones, and even some memory cards that can be inserted into older cameras can determine where you are located and record that in the metadata in the picture you take. And contrary to what you have read, new technologies do not have to use the Global Positioning System (GPS) to figure out where you are located. There are services that use WiFi to record your position. It is called WiFi Positioning System (WPS). Basically, WPS determines where it is located and communicates that to WiFi connected services so that it could be used to determine your location.
I know geotagging can be a lot of fun. A few years ago when my wife and I drove from Portland, Maine to Canada, I had taken pictures of the scenery along the way hoping to find a moose. After all, how can you go through the woods of Maine without seeing a moose?! When I loaded the pictures on my Mac in iPhoto, it was fun to see the plot of where the pictures were taken on the built-in map. I was able to follow the road into Canada just based on the geocodes.
What I did not do is post those pictures while on the road. Aside from the lack of cellular connectivity, posting those pictures would advertise to evil doers that I was not home and too far away to do anything.
If you take geocoded pictures of your coins and post them online, whether it you are posting them to a social media site or a discussion forum, you are advertising where the coin is located. This might not be a problem if you collection consists of what dealers would call ordinary or common coins. But if that 1937-D Buffalo nickel has only three legs, that geocoded picture announces that you have at least one high value coin that someone might want to acquire through less than legal means.
The problem is that I love to see pictures of interesting coins. This is one of the reasons I love Pinterest. Aside from sharing my own picture, Pinterest allows me to pin coin images from around the Internet to create virtual scrapbooks. Do you have an interesting coin? I want to see it. Different types of tokens and medals are excellent artwork.
However, when you take the pictures of your prized collection, make sure you turn off geotagging!
Unfortunately, I cannot tell you how to do it on every camera because the process is different. To help, I found the following two articles that provides an overview of how to turn off geotagging on the common smartphones:
- “How to Disable Geotagging on Your iPhone, Android Phone or Blackberry”
- “How to disable a smart phone’s geotagging feature”
For other cameras, you need to find the manual that came in the box to figure out how to do this.
In the meantime, stay safe online and let’s see those beautiful coins!
Jan 10, 2011 | commentary, security
With the news coming from Arizona this past weekend, I was thinking about personal security and the security of our collections. It may seem like a gruesome topic to discuss in the aftermath of the shooting, but as long as our attention is on the situation, we need to take a look at our own security.
Last June, I discussed the Safety and Security Traveling with Coins after the robberies of dealers traveling to and from shows. One the key points I made is the beware of your surrounding, what we call “situation awareness.” It is not typical to think like this, but if you have numismatics that seem to be desirable, you need to consider your environment. Does the area “feel right?” Do you feel comfortable in the area? Are you worried about the strangers around you? What is your gut feeling? If you are not comfortable and just have that feeling that the area is not safe, go with that feeling and take appropriate actions.
We would like to think we live in a safe neighborhood, but at least once per week I see a news report with someone saying, “Nothing like this has happened here. This is such a safe neighborhood.” Unfortunately, there is always a first time, why be the first victim. How secure is your property? Are you coins on display in your home? If they are, do you have a security system?
Whatever you have for security may not be enough. You have to think like a thief and figure out how strengthen your defenses. Sure, strengthening your defenses may stop 95-percent of the thefts, but what about the other five percent? What about the amateur thief who gets lucky?
One of the best resources you have is your home insurance company. After many years of protecting property all over the country, they know what works and where to find the best people to help. Most insurance companies will help you with the risk assessment and share with you what their company knows about the risks in your area. They can also tell you about savings that you could see if you added additional security to your home.
Aside from the security of your personal property, you also need to considered what to do with your collection when you are no longer able to enjoy it. In my post, What Will Your Heirs Do With Your Collection, I discussed the necessity of estate planning with your collection. Remember, “It may be difficult to admit that the niece or grandson that appears to love to see your coins when they visit or is excited to receive a special numismatic gift may be more happy because of their interaction with you rather than your collection.”
Be honest with yourself, does your family really want the coins or what the coins are worth. If you are not going to mind that they will sell your coins, then leave it to them. However, if they are not going to keep the collection and their disposition really matter to you, then you should figure out how to deal with them while you still can make the decision.
While we pray that Rep. Gabrielle Giffords and the others who were injured a complete recovery; and we join with the families of Judge John Roll, 9-year old Christiana Green, Dorothy Morris, Phyllis Schneck, Dorwan Stoddard, and Gabriel Zimmerman in grieving their losses, we should take this opportunity to heighten our own security awareness to protect ourselves, our loved ones, and our collections.
Jun 19, 2010 | education, security, shows
 During the last week, there were two more stories of dealers being robbed. One occurred in Witchita Falls, Texas and the other in Parisippany, New Jersey. In both cases, the dealers stopped at a restaurant after the show ended, had the windows broken to take what was in the car. The incident in Wichita Falls also involved an assault on the dealer and his wife.
During the last week, there were two more stories of dealers being robbed. One occurred in Witchita Falls, Texas and the other in Parisippany, New Jersey. In both cases, the dealers stopped at a restaurant after the show ended, had the windows broken to take what was in the car. The incident in Wichita Falls also involved an assault on the dealer and his wife.
Earlier this year, a coin dealer was robbed in Acton, Massachusetts after leaving a coin show in Westford. Also, a coin dealer from Jacksonville, North Carolina was robbed in Wilmington when he went to visit someone’s home he thought was interested in purchasing coins.
These incidents show that it is time for dealers to step up their security awareness and learn to protect themselves from the risks of robberies. Dealers with store fronts have a lot of options to protect their assets, although some have fatal ramifications. For the dealer who travels to and from shows, the security of their vehicle is very important.
During the holiday season we are reminded not to leave anything in the car that would invite someone to break in. Sometimes, you cannot fit everything in your trunk because between your clothes and inventory everything does not fit. Since many shows are one or two days, consider using a small, flat suitcase that could fit on the floor of the back seat and place it under the floor mats. It is not the best hiding place but it attracts less attention.
Aside from the usual precautions of locking doors and hiding the valuables, be particular where you park. Since thieves do not want to attract attention to themselves, park in well-lighted, crowded areas. Park close to the building especially close to the entry door. Avoid areas with trees and bushes that could be used to hide from view. Look around and think like a thief. If you can think of how to hide yourself around your car, then the thief can, too. Either find someplace else to park or another establishment for dinner.
Better security requires an investment into additional protection for your car. Car alarms are popular options and also the most hated. If not installed correctly, car alarms are prone to false alarms that can annoy everyone around. Since early car alarms did sound for seemingly no reason, some have learned to ignore them. However, the noise will draw attention to the car and scare away the thief breaking in to rob the contents. If you find an alarm with a distinctive sound you can also be quickly alerted if something happens. Car alarms range from the inexpensive that are installed by the car’s owner to a theft deterrent that could cost thousands of dollars. The website eHow.com has a good section about Car Alarm Systems to get you started.
Since many of these robberies start with someone smashing the car’s window, consider technologies that strengthen the windows. Bulletproof glass is an option, but that may be too expensive for many of us. An option is installing a laminate made from a material called polycarbonate thermoplastic over the windows. Polycarbonate thermoplastic laminates are thin, clear sheets that are sturdier than glass that does not break like glass. When installed over glass, the underlying glass will shatter but the laminate will remain intact. Thinner sheets will prevent break-ins while thicker or multiple layers can be use to make the glass bullet resistant. An auto service specializing in aftermarket add ons for cars in the Washington, D.C. metropolitan area said that it could cost from $600 to over $2,000 depending on the product used and the amount of window surface that has to be covered. There are local businesses in every major metropolitan area that can install these laminates.
Another security add-on that was recommended by the dealer was reinforced locks. A local locksmith described how easy it is to break into most cars just by using force in the right places—especially for the thief not interested in maintaining the car’s look. Although we rely on them to secure our cars, locks are a weak area in the metal and the ringed design around some locks can be pried off and the locks pulled out with a pair of pliers. Simple plates secured over the locks may act as a deterrent but may also advertise that the car may have something of value inside. Locksmiths and auto security companies can install tamper resistant locks and reinforce the area around the door, trunk, and tailgate latches to prevent someone from prying into your vehicle.
The downside to installing aftermarket tamper-resistant locks and reinforcing around the latches is that it will void the structural warranties of most vehicles. Also, poorly installed car alarms will not be covered by most vehicle warranties. Professional installation by a dealer or a qualified aftermarket seller can prevent these issues.
One call you should make is to your auto and business insurance companies. By increasing the security of your car, both insurance companies may offer discounts for lower their risk exposure. Laminates will prevent broken windows and potentially reduce the amount of money that would be necessary to fix your car to just the shattered glass and the laminate and not other items. Your business insurance may also find the lowered risk appealing since you have taken steps to prevent a potential loss. The savings may be an incentive to purchase better security for your car.
Finally, dealers must consider their situational awareness—what their surroundings look like and quickly assess what is around them. Some people may not think like this, but if you are going to carry expensive inventory and cash to and from a show you have to consider the environment. Thieves like the dark because it is easier to hide. Traveling in daylight is better than traveling during the night. But if you travel at night, stay in well lighted areas and crowded areas. What is the neighborhood like? Is it a travel stop that is used by a transient clientele? That type of movement is also inviting the thieves who knows that people traveling through those areas may have something worth stealing. Will you go into a restaurant where you cannot watch your car or should you consider a restaurant where your car is visible from within the restaurant?
Does the area “feel right?” Do you feel comfortable in the area? Are you worried about the strangers around you? What is your gut feeling? If you are not comfortable and just have that feeling that the area is not safe, go with that feeling and try another place. Consider bringing nonperishable snacks in the car so that if the first place you stop at makes you uncomfortable, you have something to tie you over until you find someplace with more comfortable surroundings.
Security is an ongoing process. Thieves will adapt and find other ways to rob you. But if you take the time to prepare yourself and pay attention to your surroundings, you should be able to reduce the risk of being robbed. Stay safe!
 One of the reasons for the delay with the Weekly World Numismatic News is that I have been looking into a report of worldwide e-commerce issues under the radar.
One of the reasons for the delay with the Weekly World Numismatic News is that I have been looking into a report of worldwide e-commerce issues under the radar. → Read more at stltoday.com
→ Read more at stltoday.com
 → Read more at kiro7.com
→ Read more at kiro7.com


 While there was plenty of news this week, I want to take this opportunity to use myself as an example. Some may have noticed that the blog was taken down for a little more than a day earlier this week. The downtime was necessary to clean up after my account was attacked.
While there was plenty of news this week, I want to take this opportunity to use myself as an example. Some may have noticed that the blog was taken down for a little more than a day earlier this week. The downtime was necessary to clean up after my account was attacked. The
The 











 While all this seems simple to me, I have been in this industry for over 30 years and am used to the complication. The problem with email is that it was developed as a way for researched to communicate by plain text across the Arpanet, the forerunner of the Internet. Essentially, email is a text-based service that has been extended in so many ways that it has created a complicated series of standards that requires a degree in computer science to analyze.
While all this seems simple to me, I have been in this industry for over 30 years and am used to the complication. The problem with email is that it was developed as a way for researched to communicate by plain text across the Arpanet, the forerunner of the Internet. Essentially, email is a text-based service that has been extended in so many ways that it has created a complicated series of standards that requires a degree in computer science to analyze.


