Weekly World Numismatic News for September 26, 2021

David J. Ryder, Director of the U.S. Mint.
Ryder served as the 34th and 39th Director after being appointed by two different administrations. Ryder came into this term touting his work with physical money security. During his confirmation hearing, Ryder said he worked for Secure Products, a company focused on developing anti-counterfeiting solutions for currency and branded products. Ryder also testified that he was involved in developing the Royal Mint’s new 12-sided one-pound coin.
The U.S. Mint claims security measures built into the new American Silver and Gold Eagle coins. However, there do not seem to be breakthroughs similar to those used by the Royal Mint and Canadian Royal Mint on their bullion products.
Ryder may want his legacy to be introducing new products, but the public will remember the colossal failure of the U.S. Mint’s e-commerce system. As Director, he was supposed to oversee the entire operation and not just one aspect. Those failures will weigh on his legacy.
Alison Doone is a career civil servant who entered the Senior Executive Service (SES) in 2004. After working at several other agencies, Doone served as the Mint’s Chief Administrative Officer since March 2021.
The Federal Vacancies Reform Act of 1998 requires the president to send a nomination to the Senate within 90 days to fill a vacant position. During that time, an acting director can serve in that role for only 180 days. As we saw in the 2,629 days (7 years, 2 months, and 13 days) between the resignation of Edmund Moy and the confirmation of David Ryder, the government has ways to get around the law to maintain operational consistency.
And now the news…
 → Read more at nmscarcheologylab.wordpress.com
→ Read more at nmscarcheologylab.wordpress.com
 → Read more at irishtimes.com
→ Read more at irishtimes.com
 → Read more at bbc.com
→ Read more at bbc.com
 → Read more at fox35orlando.com
→ Read more at fox35orlando.com
 → Read more at edition.cnn.com
→ Read more at edition.cnn.com
Phishing is back: When in doubt just delete it!
 The American Numismatic Association and Numismatic Guarantee Corporation recently issued press releases notifying the public that there have been attempted phishing scams by trying to impersonate a hotel service or someone who works for NGC. Since this is back in the news, I am taking an article I had previously written on the topic and updating it to be more current.
The American Numismatic Association and Numismatic Guarantee Corporation recently issued press releases notifying the public that there have been attempted phishing scams by trying to impersonate a hotel service or someone who works for NGC. Since this is back in the news, I am taking an article I had previously written on the topic and updating it to be more current.
Phishing is the term used to describe the attempt to convince someone to reveal personal information by sending them an email that looks like it came from a legitimate source. Unfortunately, it is so easy to spoof (trick) the Internet’s email system that all it takes is someone with attention to detail to get past spam and other security filters.
Last year, I retired as an information security professional where, for the last 25 years, was contracting to the United States government. I saw many attempted and successful attacks against both government and commercial systems. However, the one attack that is the most difficult to defend is those where humans are convinced to act against their own best interest. The technical industry calls them phishing attack but they are forms of social engineering.
A social engineering attack tries to use something about you or something you care about to convince you to do something that could potentially harm you. For example, an attacker looking to scam someone who collects rare coins may know about NGC’s business. Knowing that the people who might be using NGC’s services are collectors with a lot of disposable income, they could use the weaknesses of the email system in order to fool the recipient into a situation where they can be taken advantage of.
To help you stay safe, the following are rules you can follow to keep safe online:
Rule #1: Unless you are 100-percent certain that the email is legitimate, do not click on the link!
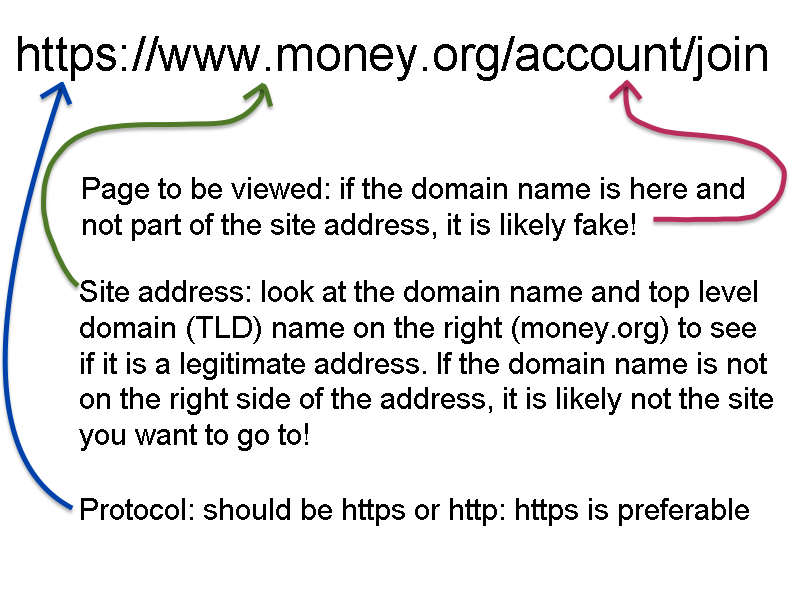
You will be never 100-percent certain that any email you receive is legitimate. Thus, make sure that you are as close as 100-percent certain as possible. One thing you can do is to move your pointer over the link, stop, and wait for the tooltip to show you the address.
Tooltips are those balloon-like popups that will tell you something about the link or element before you press the mouse button. One way to tell that a link is bad is that if the address is not what you think. For example, if the link is supposed to send you to the ANA website, the tooltip better say that it will send you to money.org. If it does not, then do not click on the link.
Place your mouse pointer over the link and let the tool tip appear. What does it say?
When you check the link, the address of the server is the first part of the address. If what should be the server name is not in that area at the beginning of the address, do not click on the link.
One trick the phishers use is to show you what looks like a complicated address in the message, but the link behind it will send you to another website. This is where tooltips can help. If you hover over the address and they do not match, it is an attempt to trick you and you should not click on the link.
If you are using a web-based email client, such as Gmail, you can check the address on the status line at the bottom of your browser window. Check to see if the address makes sense. For example, if the email claims to be from Amazon, the link should say “amazon.com” and nothing else. Sometimes phishers will try to write a link using something after the address like “amazon.com.anothersite.co” to fool you. Do not be fooled. A link like this is trying to send you to “anothersite.co” and not Amazon.
If you are unsure about the link, then go to your browser and type in the address yourself.
As with everything in life, there is an exception to the rule. Organizations, like the ANA, will use mailing list services to send out notices to members and anyone else who have signed up for these emails. Unfortunately, the URL you will click on will be one associated with the mailing list service. The service uses this to provide engagement statistics to whoever is sending out the email. For example, for the service that the ANA uses all of the links are to r.listpilot.com.
Mailing list services are great resources for many organizations and their tracking service is necessary to understand the effectiveness of the communication. If you are not sure, continue to visit the organization’s site without clicking on the link.

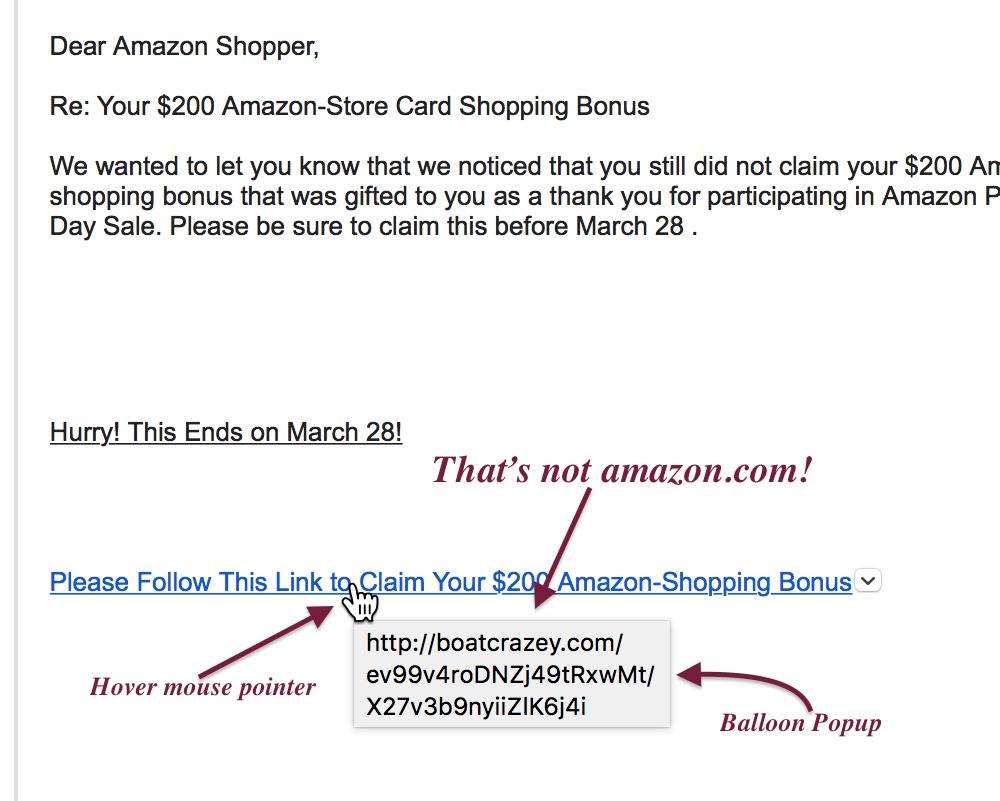
An example of an email message showing what to look for to understand how to identify it as a phishing attempt.
Rule #2: No legitimate company or organization will ask for information to be sent via email
One of the tactics that the phishers use to try to trick you into giving them your personal information is to create a form that looks like it is legitimate. Just as it is easy for someone with moderate skills to fake a web page they can also create a counterfeit form. Not only will the form be counterfeit, but they could also embed programs in that form to steal your information.
Embedded code in documents is called macros. Macros are used to command programs to do something for the user. When used in productive environments, macros can be a wonderful tool to create dynamic documents and provide input validation. But the same instructions that can make macros a productive tool can also be used to do bad things.
Unless you are certain about where the document came from, do not open a document. If you open the document and the program asks if you should enable or run macros, do not enable macros.
This is not just a problem with word processing document. PDF documents can also deliver very nasty malware (malicious software). Not only can an attacker add macros to a PDF document, but someone can embed Flash in those PDF. Flash is the technology that helps you watch online videos and add enhancements to the visual interface of some websites. But Flash can be used to attack your computer system. Opening a PDF file sent by someone you do not know can be as dangerous as a word processing document.
Rule #3: Do not open suspicious attachments
Another trick the attackers try to use is adding an attachment named in a way to entice you to open the file. File names consist of the name of a file followed by a period followed by a file extension. The file extension is used to tell the computer the type of program to execute to allow you to work with the file. There are three file extension that very dangerous and should never be opened unless you are absolutely sure who sent them: .zip, .exe, and .dmg for Mac users.
The .zip file extension tells the computer that the file is something called a Zip archive. A Zip archive is a file that is formatted to allow it to store many files that are compressed. Zip files are used for many legitimate purposes including being the default format of Microsoft Word’s .docx file. Unfortunately, it can contain programs and files that can be used to attack your system.
One of the types of file that can be included in a Zip archive is a .exe or executable file. Simply, these are programs in the same way that Microsoft Word is a program. Once an executable file is opened, it will do whatever it is programmed to do. Among the things that the program can do is keylogging. A keylogger reads what you type on your keyboard, what you click on the screen, and in some cases, what is displayed on your screen. The keylogger will be able to capture the username and password you entered when you visit any website including your bank’s website. The problem is that when a key logging program is run, you do not know it is watching what you type. Nor do you know that it connects to a server somewhere on the Internet to send the information to the attacker. Keyloggers and other malware can infect your system in a way that allows it to continue to exist, even if you reboot the computer.
You may ask about anti-virus software helping stop malware. Anti-virus software is programmed to understand what is known about attack vectors. It cannot protect you if it does not know how the virus works. Remember that the government warned that last year’s flu vaccine was not effective for the version of the virus infecting people? Anti-virus software is similar that if it doesn’t know about the strain it cannot protect you. Hackers are always looking for ways to fool anti-virus software.
For Windows user, you should consider running Windows Defender. Windows Defender is built into Windows but cannot be run if you have another anti-virus software. I use Windows Defender and have been happy with the results. If you want more information about Windows Defender visit this page on Microsoft’s support site.
While Macs are more difficult to attack they are not immune. Mac users should never open a file with a .dmg file extension unless you know who sent the file. The Macintosh .dmg file is a disk image stored as a regular file. A disk image file is formatted to look and acts like a disk so that when you double-click the icon, it will mount on your computer as if you plugged in an external disk drive. Because .dmg files are commonly used to install legitimate software, sometimes the installation can be automatically started. If you allow the installation to continue, you can install software as dangerous as what I described for the Windows .exe file.
OS X is a different type of operating system where if you are careful you can get away without running an anti-virus program. However, if you want to be paranoid (along with me) you might want to run the free anti-malware software from Malware Bytes.
Regardless of the operating system and software you use, ALWAYS KEEP IT UP TO DATE! Patching your computer may be an annoyance but the dangers, if you do not apply security patches, will hurt more and last longer!
Rule #4: When in doubt, throw it out!
 While all this seems simple to me after having worked in this industry for nearly 40 years, I have seen how these concepts are confusing to the non-technical user. The problem with email is that it was developed as a way for researchers to communicate by plain text across Arpanet, the forerunner of the Internet. Email, as a text-based service, \ has been extended in so many ways that it has created a complicated series of standards that require a degree in computer science to analyze. While these complications make it easier to communicate via email it also makes it difficult to secure.
While all this seems simple to me after having worked in this industry for nearly 40 years, I have seen how these concepts are confusing to the non-technical user. The problem with email is that it was developed as a way for researchers to communicate by plain text across Arpanet, the forerunner of the Internet. Email, as a text-based service, \ has been extended in so many ways that it has created a complicated series of standards that require a degree in computer science to analyze. While these complications make it easier to communicate via email it also makes it difficult to secure.
Even if you cannot fully analyze whether the message is spam or legitimate, if you have any doubt, then just press the delete button. If the message came from a source you know, contact them off-line and ask if the mail is legitimate. If you think the email is from your bank, call the bank and ask. If you think the email is from your credit card company but not sure, call the credit card provider and ask. If you think the email sent from the ANA or NGC is suspicious, call them and ask.
A little intuition and some due diligence can be of great help in these circumstances.
Stay safe online!
Susie B still fools people today

A 1979-D Susan B Anthony dollar found in change that was mistaken for a quarter.
This week, I was involved in a real-life example of this confusion.
While getting ready to retire for the evening, I empty my pockets on my dresser and look to see if there is anything interesting. Since my only trip of the day was a local grocery store, I did not expect anything. As I looked at what I thought was 78-cents something did not look right. As it turned out, one of the quarters was not a quarter.
Mixed in with the change from my single transaction of the day was a 1979-D Susan B. Anthony dollar coin. Not only did the cashier make the mistake, but when I accepted the change I did not catch the difference.
A real-life example as to the reason why the Susie B. was not a successful coin!
Online Research Resources UPDATE: Currency
 Last week, I posted an article about online resources that I use when I want to begin research on a numismatic topic. The list provided a number of resources but a reader wrote to me and noted that I forgot to include paper money resources beyond the Bureau of Engraving and Printing.
Last week, I posted an article about online resources that I use when I want to begin research on a numismatic topic. The list provided a number of resources but a reader wrote to me and noted that I forgot to include paper money resources beyond the Bureau of Engraving and Printing.
Paper Money Sources
When it comes to searching for information on paper money, I always start at one of the following three sites:
- USPaperMoney.Info
- Don and Vic’s World Banknote Gallery: worldbanknotegallery.com
- Banknote News: banknotenews.com
The opening line at USPaperMoney.Info says that it is the “home of everything you ever wanted to know about U.S. currency. (Well, almost….)” This is truth in advertising. Even with the page of unanswered questions, the site has everything you could ever want to know about U.S. currency. I just wish the author would organize the site better.
Don and Vic’s World Banknote Gallery is one of those sites that looks like it was created by a seventh grader in 1998 but has a tremendous amount of very useful information. It is one of the best sites I have found to identify world banknotes.
They have a companion site named World Coin Gallery that is similar. I have used this site and have added it to the original bookmarks file. If you downloaded the original bookmarks then right-click (Control-click for Mac users) and select the option to add worldcoingallery.com to your bookmarks.
Last, but definitely not least, is Banknote News by Owen Linzmayer. If you want to know anything about the production of world paper money, this is the site you need to read. In addition to the information, which a lot of it is in blog form and consistently tagged for easy navigation, Linzmayer has also compiled one of the best references on world paper money called The Banknote Book. He said he did this because he and other collectors were frustrated with the “many errors, omissions, and poor-quality images” in the Standard Catalog of World Paper Money.
The Banknote Book can be purchased as a physical book as a three-volume set complete through 2014 or you can buy individual chapters corresponding to the country of your interest.
If you want to check it out for yourself, download 17 Free Sample Chapters and judge for yourself.
Currency Bookmarks
Do you want to add these links to your browser’s bookmarks? Right-click (or Mac users can CTRL-Click) on the following button and select whatever option your browser requires to save the file to hard drive. Import the file as an “HTML Bookmark” file to add these links to your bookmarks.
March 2018 Numismatic Legislation Review
 While Congress delves into the abyss of their usual folly, the numismatic industry went almost hysterical at the bill introduced by Rep. Barbara Lee (D-CA) to create yet another quarters series to begin in 2021.
While Congress delves into the abyss of their usual folly, the numismatic industry went almost hysterical at the bill introduced by Rep. Barbara Lee (D-CA) to create yet another quarters series to begin in 2021.
Not considering the topic, there is a fatigue over changing quarter designs. The 50 State Quarter Series was a success while economic times were good and the states were taking their responsibility for designing the quarters serious. Some states really missed out on good design and good choices that there are some quarters that should be melted and spared from our change.
And while there have been wonderful designs for the America the Beautiful quarters, the response has been anywhere from underwhelming to non-existent. Few people know the series exists and when it is pointed out to them there is a collective shrug of acknowledgment.
The other problem goes to the mouth-breathing aspect of the coverage in that the bill was just introduced into the House of Representatives, it is not the law. It is a long way from a bill being a law. If you forgot the process you can always rewatch the old Schoolhouse Rock video I’m Just a Bill.
For the record, I have no problem with honoring the Nineteenth Amendment and the women who made it possible. I would also have no problem with a coin program honoring the Fourteenth Amendment and the people involved in Civil Rights. This country can use a dose of education and if it can be done using coinage, then maybe I might reconsider my stance on the ever-changing coin designs.
At least David Ryder’s nomination was confirmed!
PN1355: David J. Ryder — Department of the Treasury
H.R. 5308: Women’s History and Nineteenth Amendment Centennial Quarter Dollar Coin Program Act
Weekly World Numismatic News for April 1, 2018 (No Fooling!)

Philippines Rep. Jericho Nograles holds newly release BSP coins noting they “are misleading the public and are causing a lot of confusion.” (Miguel de Guzman of the Philippines Star.)
For those who did not have the pleasure of accidentally spending the dollar coin as a quarter, the Susie B. was too close to the size to the Washington quarter, had reeded edges like the Washington quarter, and on a simple glance was consistently confused with the Washington quarter. The confusion made the coin very unpopular in the United States even though it continues to find usage in other countries whose currency is based on the U.S. dollar.
In the Philippines, the BSP made the mistake of making the one-peso and five-peso coins very similar in size, look, and feel. It is so bad that a member of the Philippines Congress is urging the BSP to recall the coins.
“Basic design principles for coinage demand that the denominations are easy to distinguish not just visually, but also through touch or tactile differences,” said Rep. Jericho Nograles. “Our new coins fail in these principles.”
The story almost reads like discussions others have had with coin design issues when Nograles asks, “Did the BSP consider jeepney, pedicab, tricycle and taxi drivers? Did they consider the visually impaired, and senior citizens, at all?”
They likely did not and will have to be dragged into reality kicking and screaming like the Bureau of Engraving and Printing had to be over the same issues.
And now the news…
You may want to check your pockets to look for one of the most elusive Korean coins there is — the 1998 500 won coin. Though the odds of you finding one of these coins is almost nil, you never know when you might just hit the jackpot — stranger things have happened.  → Read more at korea.stripes.com
→ Read more at korea.stripes.com
A hoard of rare bronze Jewish Revolt coins has been discovered at the recently renewed Ophel excavations. The trove of dozens of bronze coins minted during the last years of the ill-fated four-year rebellion of the Jews against Roman rule was uncovered in a cave just south of the Temple Mount by Hebrew University archaeologist Dr.  → Read more at timesofisrael.com
→ Read more at timesofisrael.com
KUMAGAYA, Saitama Prefecture — One of the biggest hauls of medieval coins ever discovered in Japan has been unearthed in Saitama Prefecture. Tens of thousands of bronze coins were found in a buried ceramic jar believed to date back to the first half of the 15th century.  → Read more at asahi.com
→ Read more at asahi.com
MANILA, Philippines — Rep. Jericho Nograles of party-list group Puwersa ng Bayaning Atleta yesterday urged the Bangko Sentral ng Pilipinas (BSP) to immediately recall all its newly released coins due to “serious design flaws.”  → Read more at philstar.com
→ Read more at philstar.com
The first coins to be issued marking the reign of King Rama X will be put into circulation on April 6, Finance Minister Apisak Tantivorawong said on Wednesday. The new coins would replace existing coins, which were exiting the economy.  → Read more at bangkokpost.com
→ Read more at bangkokpost.com
The decision of the Bangko Sentral ng Pilipinas to introduce a new series of coins was meant to deter foreign entities from stealing large quantities of the local specie to extract their nickel content.  → Read more at business.inquirer.net
→ Read more at business.inquirer.net
The Queen carries out the Royal Maundy service at Windsor Castle without the Duke of Edinburgh.  → Read more at bbc.com
→ Read more at bbc.com
Three new glow-in-the-dark starship coins are coming soon, courtesy of the Royal Canadian Mint.  → Read more at trektoday.com
→ Read more at trektoday.com